Fixing Issues and Remediation
Transform your AI Scanner findings into secure, high-quality code using intelligent fix recommendations, automated patches, and proven remediation strategies.
One-Click AI-Powered Fixes
The most powerful feature of AI Scanner is the ability to automatically fix many detected issues with a single click.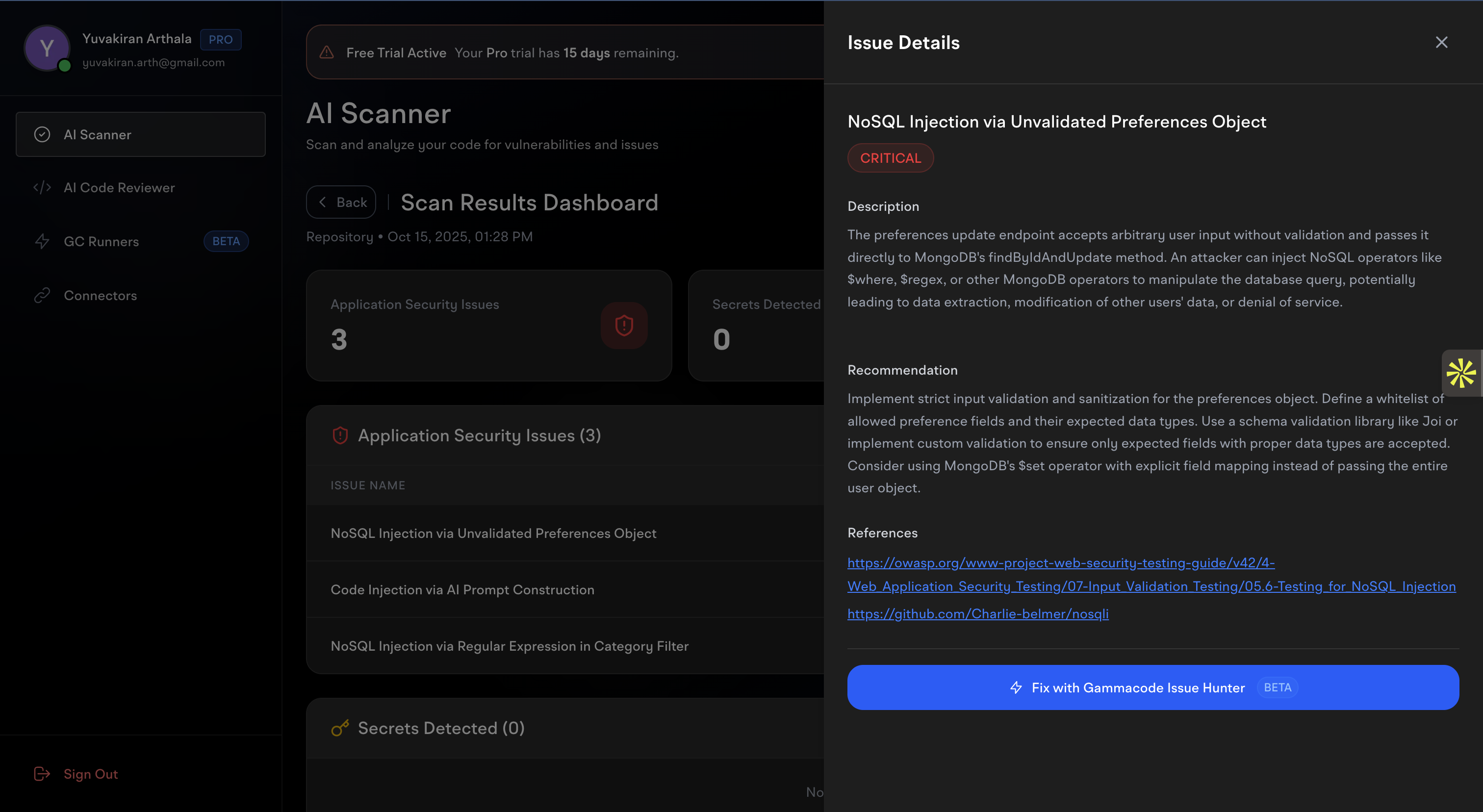
How One-Click Fixes Work
When viewing an issue’s details, you’ll see the “Fix with Gammacode Issue Hunter” button for issues that support automated remediation:- Analysis - AI examines the vulnerable code and surrounding context
- Solution Generation - Creates a secure, tested fix that preserves functionality
- Code Replacement - Applies the fix directly to your repository
- Verification - Ensures the fix doesn’t break existing functionality
Supported Fix Types
Injection Vulnerabilities
- SQL Injection - Converts to parameterized queries
- NoSQL Injection - Implements proper input validation
- Command Injection - Sanitizes system commands
- XSS Prevention - Adds output encoding and validation
Authentication & Authorization
- Weak Authentication - Strengthens authentication mechanisms
- Session Management - Implements secure session handling
- Access Control - Adds proper authorization checks
- Password Security - Improves password handling
Data Security
- Encryption Issues - Implements proper encryption
- Data Validation - Adds input sanitization
- Output Encoding - Prevents data leakage
- Secure Headers - Adds security headers
Manual Remediation Strategies
For issues that require manual intervention, AI Scanner provides comprehensive guidance.Understanding the Vulnerability
Before fixing any issue, ensure you understand:Root Cause Analysis
- What makes this code vulnerable?
- How could an attacker exploit this?
- What data or functionality is at risk?
- What are the business implications?
Impact Assessment
- Confidentiality Impact - Could sensitive data be exposed?
- Integrity Impact - Could data be modified or corrupted?
- Availability Impact - Could the system be disrupted?
- Compliance Impact - Does this affect regulatory requirements?
Common Remediation Patterns
Input Validation and Sanitization
Problem: Unvalidated user input leads to injection attacks Solution Pattern:- Validate all input at application boundaries
- Use whitelist validation when possible
- Sanitize data before processing
- Use parameterized queries for database operations
Output Encoding
Problem: Unencoded output enables XSS attacks Solution Pattern:- Encode output based on context (HTML, JavaScript, CSS, URL)
- Use framework-provided encoding functions
- Never trust user-provided content
- Implement Content Security Policy (CSP)
Authentication Strengthening
Problem: Weak authentication mechanisms Solution Pattern:- Use strong hashing algorithms (bcrypt, Argon2)
- Implement account lockout mechanisms
- Add multi-factor authentication
- Use secure session management
Authorization Implementation
Problem: Missing or inadequate access controls Solution Pattern:- Implement role-based access control (RBAC)
- Verify permissions for every request
- Use principle of least privilege
- Implement defense in depth
Secure Coding Best Practices
Security by Design
Threat Modeling
- Identify Assets - What needs protection?
- Identify Threats - What could go wrong?
- Assess Risk - What’s the likelihood and impact?
- Design Controls - How to mitigate risks?
Secure Development Lifecycle
- Requirements - Include security requirements
- Design - Design security controls
- Implementation - Follow secure coding practices
- Testing - Include security testing
- Deployment - Secure configuration
- Maintenance - Regular security updates
Framework-Specific Guidance
Node.js / Express Security
React Security
Python Flask Security
Secret Remediation
Immediate Response to Exposed Secrets
Step 1: Assess the Exposure
- What type of secret was exposed?
- How long was it accessible?
- What systems does it provide access to?
- Who might have had access to the repository?
Step 2: Revoke Compromised Credentials
- Immediately revoke the exposed credentials
- Generate new credentials with appropriate permissions
- Update applications to use new credentials
- Monitor for unauthorized access using the old credentials
Step 3: Remove from Version History
Step 4: Implement Secret Management
- Use environment variables for configuration
- Implement secret management tools (HashiCorp Vault, AWS Secrets Manager)
- Use CI/CD secret injection for deployment credentials
- Implement secret scanning in your development workflow
Preventing Future Secret Exposure
Development Practices
Pre-commit Hooks
Testing Your Fixes
Verification Strategies
Functional Testing
- Unit Tests - Ensure fixes don’t break functionality
- Integration Tests - Verify system components work together
- End-to-End Tests - Test complete user workflows
- Regression Tests - Ensure old issues don’t reappear
Security Testing
- Re-scan with AI Scanner - Verify issues are resolved
- Penetration Testing - Manual testing of security controls
- Code Review - Peer review of security fixes
- Static Analysis - Additional automated security scanning
Performance Testing
- Load Testing - Ensure security fixes don’t impact performance
- Stress Testing - Verify system stability under load
- Resource Monitoring - Check memory and CPU usage
- Response Time Analysis - Monitor application responsiveness
Building a Security Culture
Team Education
Security Training
- Regular Security Workshops - Keep team updated on threats
- Code Review Training - Teach secure code review practices
- Incident Response Training - Prepare for security incidents
- Tool Training - Ensure team knows how to use security tools
Knowledge Sharing
- Security Champions - Designate security advocates on each team
- Brown Bag Sessions - Regular informal security discussions
- Documentation - Maintain security guidelines and standards
- Lessons Learned - Share insights from security incidents
Process Integration
Development Workflow
- Security Requirements - Include in project planning
- Secure Design - Review designs for security implications
- Secure Implementation - Follow secure coding practices
- Security Testing - Include in testing procedures
- Security Review - Review before deployment
- Monitoring - Continuous security monitoring
Continuous Improvement
- Regular Security Assessments - Periodic security reviews
- Metrics Tracking - Monitor security improvement trends
- Tool Evaluation - Regularly assess security tooling
- Process Refinement - Continuously improve security processes