Viewing and Understanding Scan Results
Master the AI Scanner dashboard to effectively interpret security findings, understand vulnerability details, and prioritize remediation efforts for your codebase.
Navigating the Results Dashboard
After your scan completes, the results dashboard provides a comprehensive overview of your code’s security and quality status.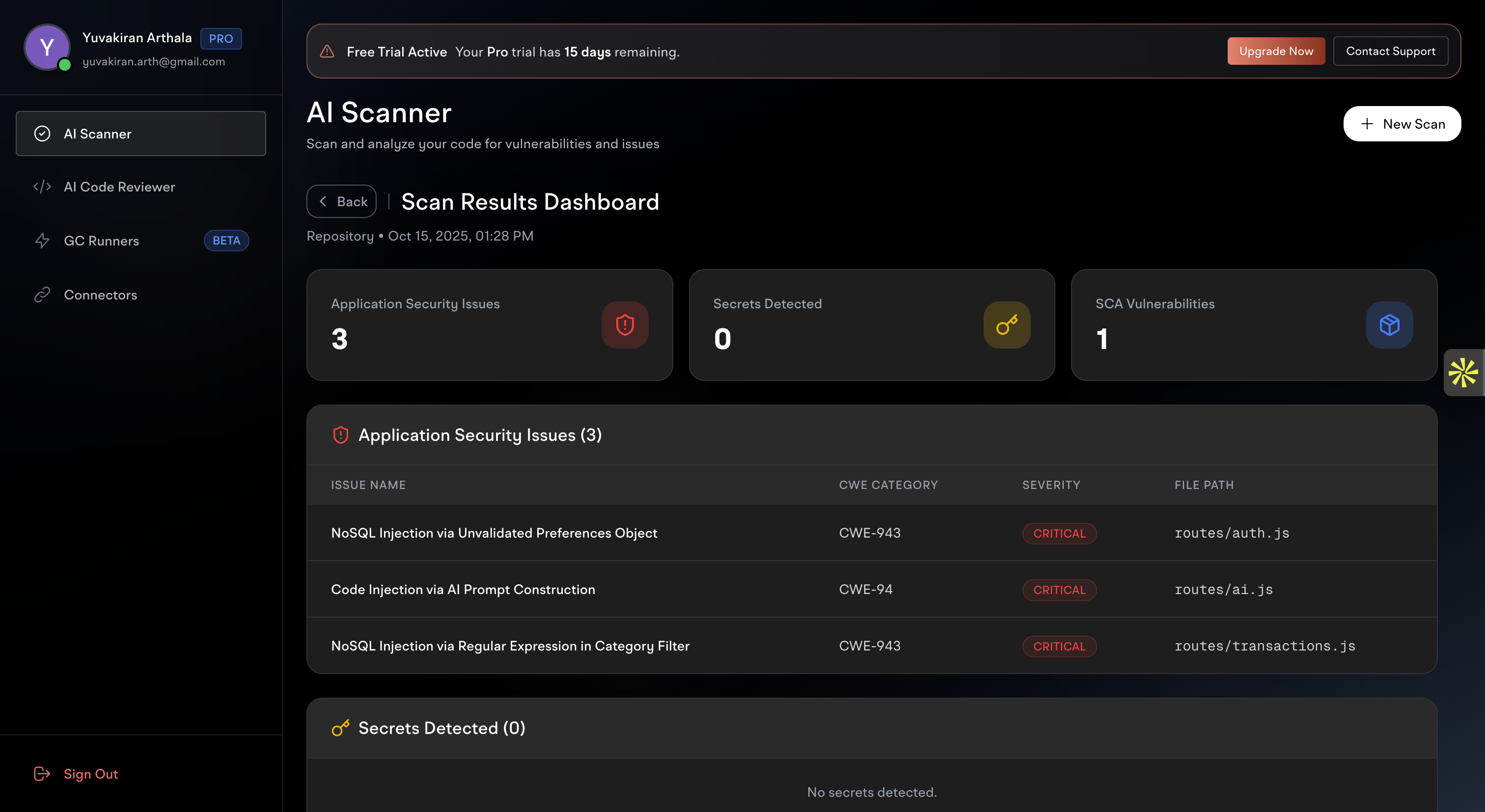
Overview Cards
The top section displays high-level metrics:Application Security Issues
- Count: Total number of security vulnerabilities detected
- Types: Injection flaws, authentication issues, authorization problems
- Impact: Critical security risks requiring immediate attention
Secrets Detected
- Count: Number of exposed secrets found in your code
- Types: API keys, passwords, tokens, certificates
- Risk: Potential for unauthorized access to services and data
SCA Vulnerabilities
- Count: Software Composition Analysis findings
- Types: Known CVEs in dependencies, outdated packages
- Impact: Third-party security risks and compliance issues
Detailed Issue Listings
Below the overview cards, you’ll find comprehensive tables showing:Issue Information
- Issue Name - Clear, descriptive title of the vulnerability
- CWE Category - Common Weakness Enumeration classification
- Severity Level - Critical, High, Medium, or Low priority
- File Path - Exact location in your repository
Understanding Issue Details
Click on any issue to open the detailed analysis panel: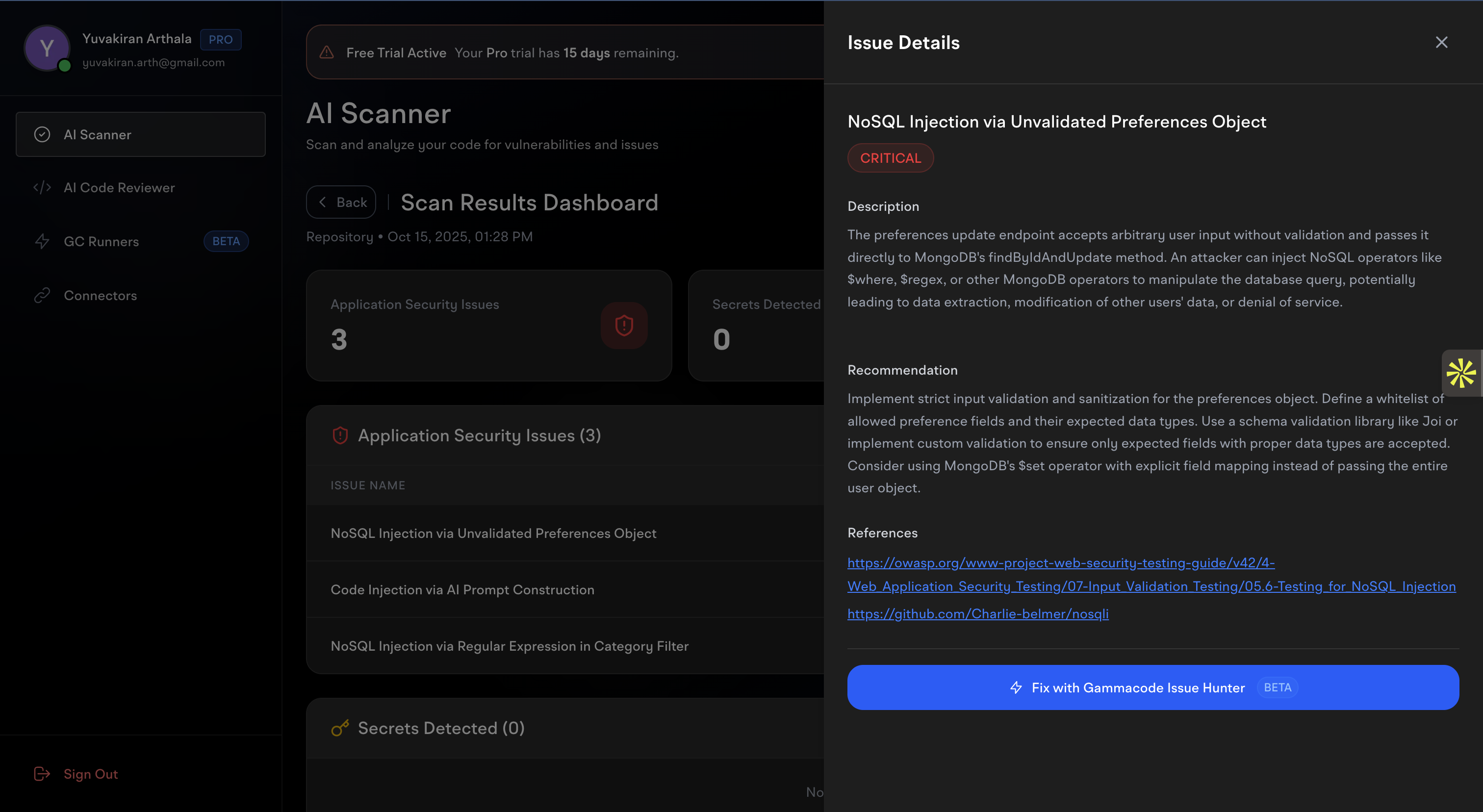
Issue Detail Components
Vulnerability Description
- Technical Explanation - How the vulnerability works
- Attack Vectors - Ways an attacker could exploit this issue
- Impact Assessment - Potential consequences of exploitation
- Context - Where and why this issue occurs in your code
Recommendations
- Fix Strategy - Step-by-step remediation approach
- Code Examples - Before and after code snippets
- Best Practices - How to prevent similar issues
- Security Guidelines - Industry standard recommendations
References and Resources
- OWASP Links - Open Web Application Security Project resources
- CWE Details - Common Weakness Enumeration information
- Security Guides - Additional reading and documentation
- Tool Documentation - Framework-specific security guides
Severity Classification
Critical Issues 🔴
Immediate Action Required- High probability of exploitation
- Severe impact on confidentiality, integrity, or availability
- Could lead to complete system compromise
- Examples: SQL injection, authentication bypass, remote code execution
High Issues 🟠
Address in Current Sprint- Significant security impact
- Moderate to high exploitability
- Could expose sensitive data or functionality
- Examples: XSS vulnerabilities, weak cryptography, privilege escalation
Medium Issues 🟡
Plan for Next Release- Moderate security or quality impact
- Lower probability of exploitation
- Could affect system reliability or maintainability
- Examples: information disclosure, denial of service, code quality issues
Low Issues ⚪
Address During Maintenance- Minor security or quality improvements
- Best practice recommendations
- Primarily affects code maintainability
- Examples: missing security headers, code smells, documentation gaps
Common Vulnerability Types
Injection Vulnerabilities
SQL Injection (CWE-89)
- Risk: Database compromise, data theft
- Detection: Unsanitized user input in SQL queries
- Fix: Use parameterized queries, input validation
NoSQL Injection (CWE-943)
- Risk: Database manipulation, unauthorized access
- Detection: Direct object construction from user input
- Fix: Input validation, query parameterization
Code Injection (CWE-94)
- Risk: Remote code execution, system compromise
- Detection: Dynamic code evaluation with user input
- Fix: Avoid eval(), use safe alternatives
Authentication & Authorization
Broken Authentication (CWE-287)
- Risk: Unauthorized access, account takeover
- Detection: Weak password policies, session management
- Fix: Strong authentication, secure session handling
Missing Authorization (CWE-862)
- Risk: Access to restricted resources
- Detection: Unprotected endpoints, missing access controls
- Fix: Implement proper authorization checks
Data Exposure
Sensitive Data Exposure (CWE-200)
- Risk: Information leakage, privacy violations
- Detection: Unencrypted sensitive data, verbose errors
- Fix: Encrypt data, sanitize error messages
Insecure Direct Object References (CWE-639)
- Risk: Unauthorized data access
- Detection: Direct database IDs in URLs
- Fix: Use indirect references, authorization checks
Secret Detection Results
Types of Secrets Detected
API Keys and Tokens
- AWS Access Keys - Cloud service credentials
- Database Passwords - Connection string credentials
- OAuth Tokens - Application authorization tokens
- Third-party API Keys - Service integration credentials
Certificates and Keys
- Private Keys - Cryptographic private keys
- SSL Certificates - Web server certificates
- SSH Keys - Server access keys
- Signing Certificates - Code signing certificates
Secret Risk Assessment
High Risk Secrets
- Production Credentials - Live service access
- Administrative Access - High-privilege accounts
- Financial Services - Payment processing keys
- Personal Data Access - PII database credentials
Medium Risk Secrets
- Development Credentials - Test environment access
- Limited Scope Keys - Restricted service access
- Expired Credentials - Time-limited tokens
- Read-only Access - Limited permission keys
Software Composition Analysis (SCA)
Dependency Vulnerabilities
Known CVEs
- Critical Vulnerabilities - Publicly disclosed security flaws
- Exploit Availability - Active exploits in the wild
- CVSS Scores - Industry standard vulnerability scoring
- Patch Availability - Updated versions with fixes
Outdated Dependencies
- Security Updates - Versions with security patches
- Breaking Changes - Major version updates required
- Maintenance Status - Actively maintained packages
- Alternative Packages - Replacement recommendations
License Compliance
- License Conflicts - Incompatible license combinations
- Commercial Restrictions - Usage limitations
- Attribution Requirements - Required license notices
- Copyleft Obligations - Distribution requirements
Filtering and Sorting Results
Filter Options
- By Severity - Show only Critical, High, Medium, or Low issues
- By Type - Security, Quality, Secrets, or SCA findings
- By File - Issues in specific files or directories
- By Status - New, In Progress, or Resolved issues
Sorting Options
- By Severity - Most critical issues first
- By File Path - Organized by location in codebase
- By Issue Type - Grouped by vulnerability category
- By Detection Date - Most recently found issues first
Exporting and Sharing Results
Export Formats
- PDF Reports - Executive summaries and detailed findings
- CSV Data - Spreadsheet-compatible issue lists
- JSON Export - Machine-readable results for integration
- SARIF Format - Static Analysis Results Interchange Format
Report Customization
- Executive Summary - High-level overview for management
- Technical Details - Detailed findings for developers
- Compliance Reports - Formatted for security audits
- Trend Analysis - Progress tracking over time
Taking Action on Results
Immediate Actions
- Review Critical Issues - Address highest-risk vulnerabilities first
- Secure Exposed Secrets - Rotate compromised credentials immediately
- Block Deployments - Prevent vulnerable code from reaching production
- Notify Team - Alert relevant team members about findings
Planning Remediation
- Prioritize by Risk - Focus on exploitable vulnerabilities
- Estimate Effort - Plan development time for fixes
- Assign Ownership - Designate team members for each issue
- Set Deadlines - Establish realistic remediation timelines
Tracking Progress
- Create Tickets - Use project management tools to track fixes
- Regular Reviews - Weekly security review meetings
- Re-scan After Fixes - Verify issues are resolved
- Trend Monitoring - Track security improvements over time