AI Scanner (Issue Hunters)
AI Scanner is Gammacode’s intelligent web-based code analysis tool that scans your GitHub repositories for security vulnerabilities, secrets, and code quality issues with detailed recommendations and one-click fixes.
What is AI Scanner?
AI Scanner is a powerful web-based tool accessible at https://gammacode.dev/profile that provides:- Security Analysis - Detect vulnerabilities, injection flaws, and security weaknesses
- Secret Detection - Find exposed API keys, passwords, and sensitive data
- Code Quality Analysis - Identify code smells, performance issues, and maintainability problems
- SCA Vulnerabilities - Software Composition Analysis for dependency vulnerabilities
- One-Click Fixes - AI-powered automatic fixes for detected issues
- Detailed Reports - Comprehensive scan results with CWE categorization
How AI Scanner Works
1. Connect Your GitHub Account
First, you’ll need to authenticate with GitHub through OAuth to access your repositories:- Visit https://gammacode.dev/profile
- Sign in to your Gammacode account
- Click “Connect GitHub” to authorize repository access
- Grant permissions for the repositories you want to scan
2. Access AI Scanner
Once your GitHub account is connected:- Navigate to the AI Scanner section in your dashboard
- You’ll see your scan history and available scan types
- If you haven’t run any scans yet, you’ll see an empty dashboard
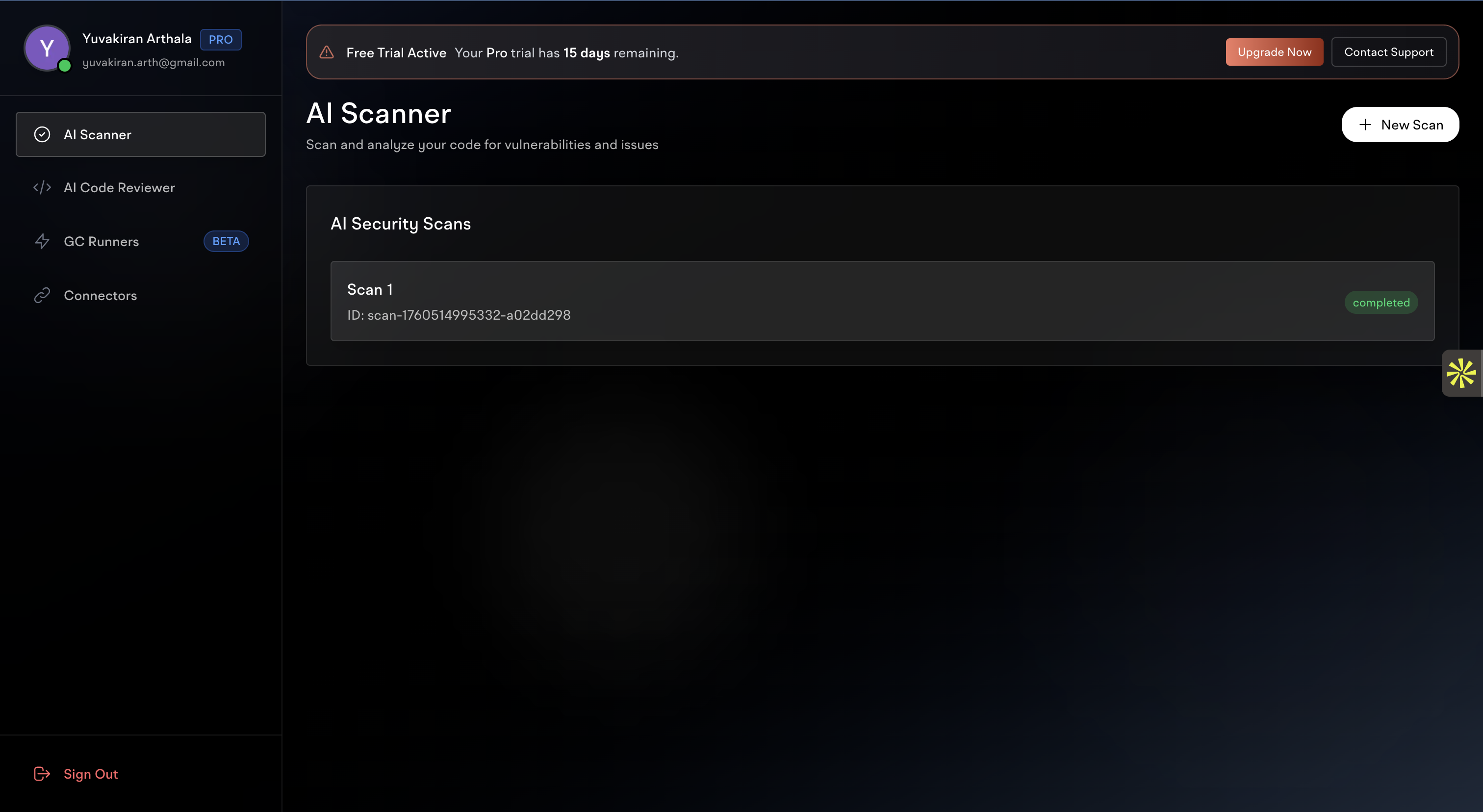
- AI Security Scans - Your completed security analysis scans
- New Scan button to start a new analysis
- Scan history with completion status and IDs
3. Start a New Scan
Click the “New Scan” button to begin analyzing a repository: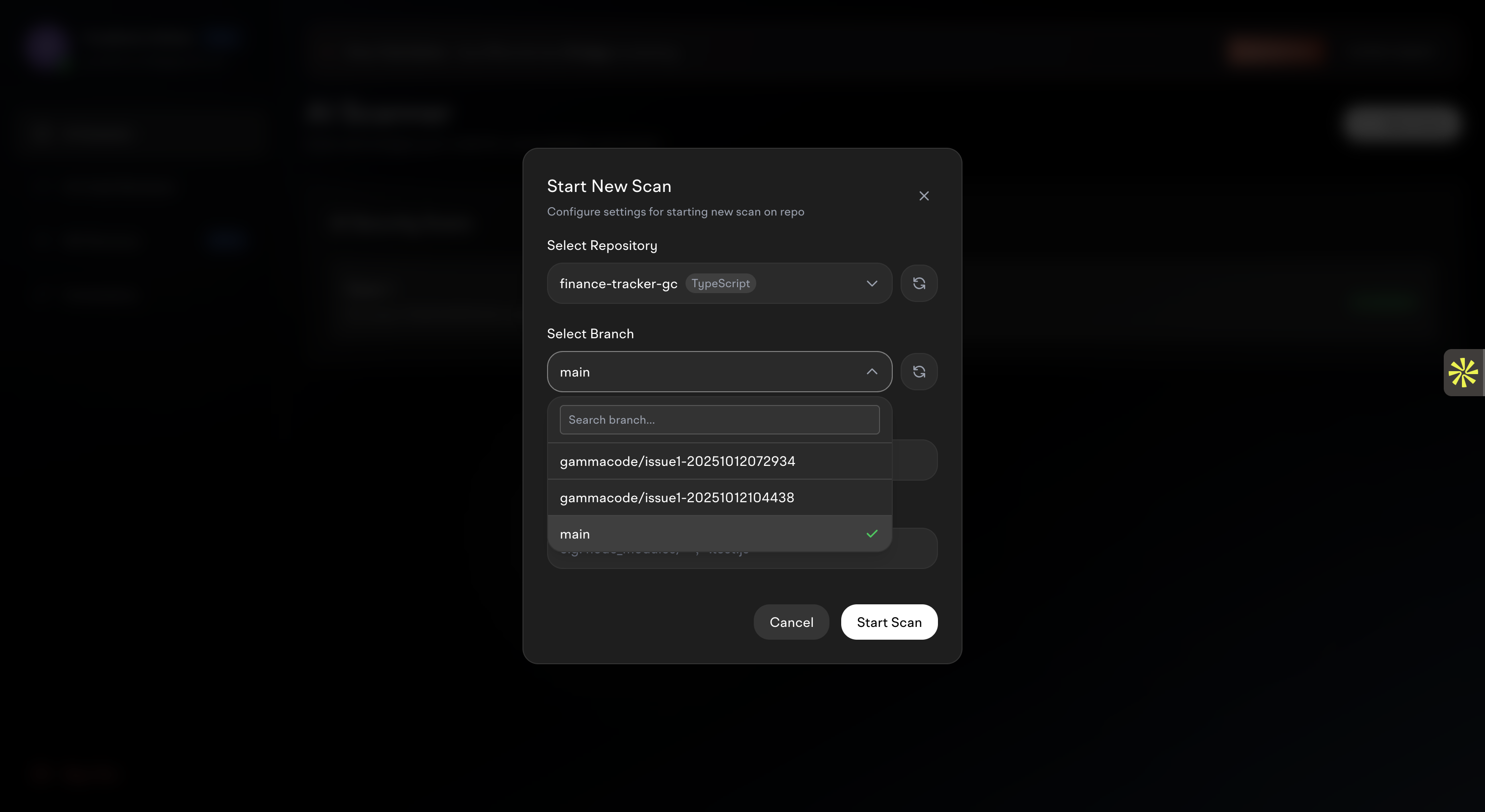
- Select Repository - Choose from your connected GitHub repositories
- Select Branch - Pick the specific branch to analyze (main, develop, feature branches)
- Configure Settings - Set scan parameters and preferences
4. View Scan Results
After the scan completes, you’ll see a comprehensive dashboard with your results: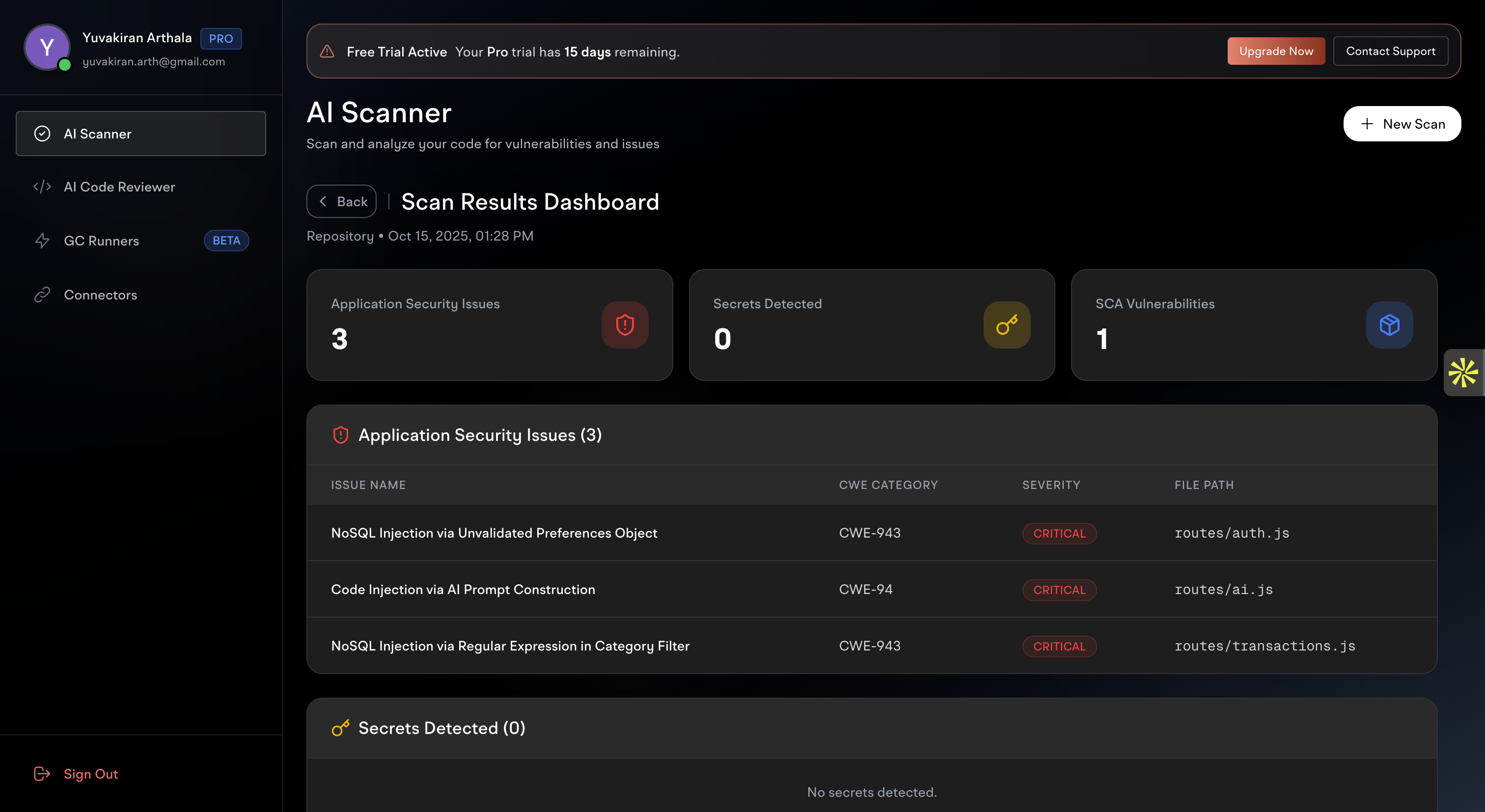
Security Overview Cards
- Application Security Issues - Count of detected security vulnerabilities
- Secrets Detected - Number of exposed secrets found
- SCA Vulnerabilities - Software composition analysis findings
Detailed Issue Lists
- Issue Name - Clear description of each vulnerability
- CWE Category - Common Weakness Enumeration classification
- Severity Level - Critical, High, Medium, or Low priority
- File Path - Exact location of the issue in your codebase
5. Fix Issues with One Click
Click on any issue to see detailed information and get AI-powered fixes: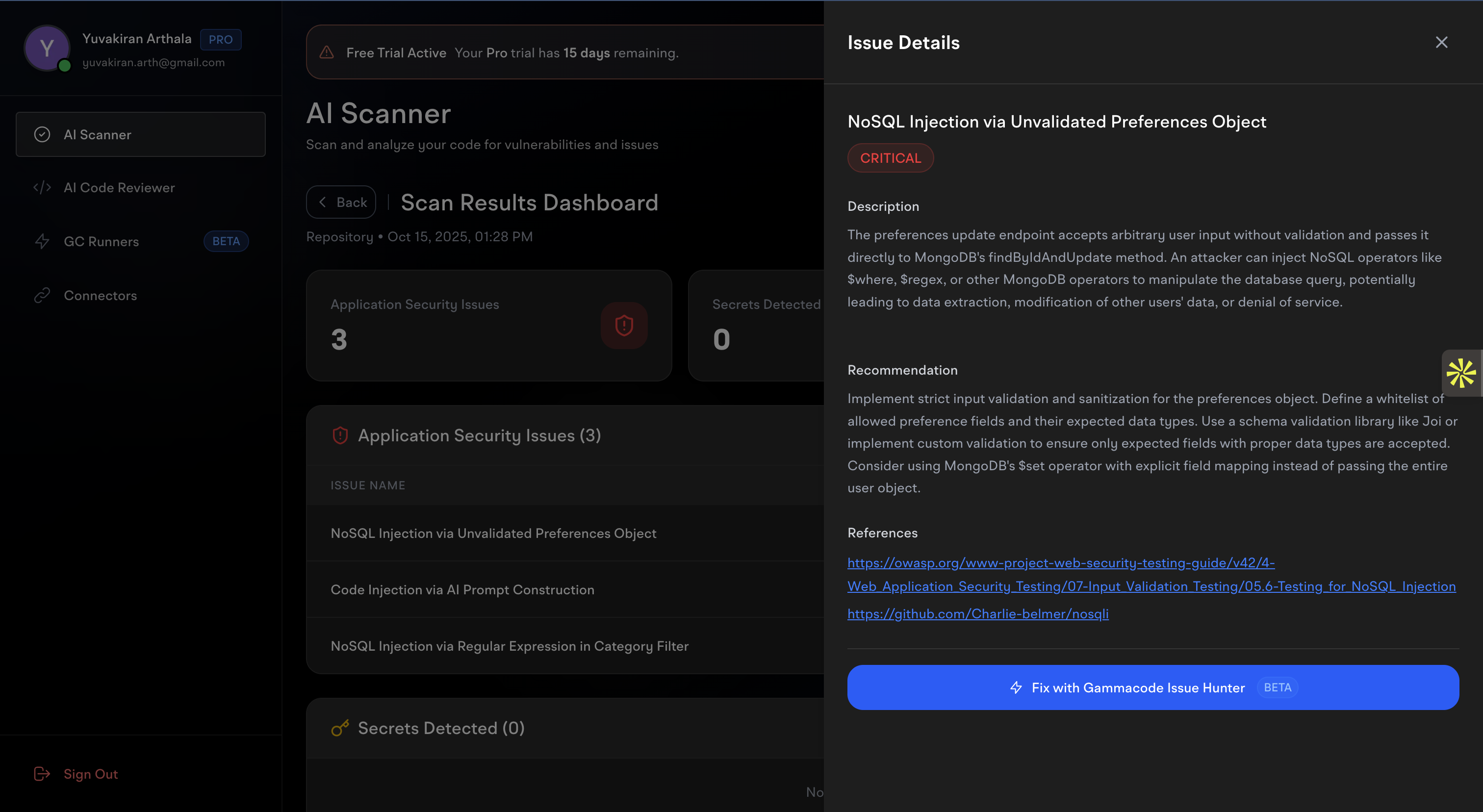
- Complete Description - Detailed explanation of the vulnerability
- Security Impact - What risks this issue poses to your application
- Recommendation - Step-by-step guidance for fixing the issue
- References - Links to security resources and documentation
- Fix with Gammacode Issue Hunter - One-click AI-powered fix button
Types of Analysis
Security Analysis
Detects critical security vulnerabilities including:- Injection Flaws - SQL injection, NoSQL injection, command injection
- Authentication Issues - Weak authentication, session management problems
- Authorization Flaws - Access control vulnerabilities
- Data Validation - Input validation and sanitization issues
- Cryptographic Issues - Weak encryption, insecure hashing
Secret Detection
Finds exposed sensitive information:- API Keys - Third-party service keys and tokens
- Database Credentials - Passwords and connection strings
- Certificates - Private keys and certificates
- OAuth Tokens - Access tokens and refresh tokens
- Custom Secrets - Application-specific sensitive data
Code Quality Analysis
Identifies maintainability and performance issues:- Code Smells - Duplicated code, long methods, complex functions
- Performance Issues - Inefficient algorithms, memory leaks
- Best Practices - Coding standards and framework conventions
- Maintainability - Code structure and organization problems
SCA (Software Composition Analysis)
Analyzes your dependencies for:- Known Vulnerabilities - CVE-identified security issues
- Outdated Packages - Dependencies with available security updates
- License Issues - Licensing compliance and conflicts
- Dependency Conflicts - Version conflicts and compatibility issues
Scan Types Available
Quick Security Scan
- Focuses on critical security vulnerabilities
- Fast analysis for immediate security insights
- Ideal for regular security checks
Comprehensive Analysis
- Full security, quality, and dependency analysis
- Detailed reports with extensive recommendations
- Best for thorough code reviews and audits
Custom Scans
- Configure specific analysis rules
- Focus on particular file types or directories
- Tailored for specific project requirements
Understanding Results
Severity Levels
Critical 🔴- Immediate security risks requiring urgent attention
- High probability of exploitation
- Potential for data breaches or system compromise
- Significant security or quality issues
- Should be addressed in current development cycle
- Notable impact on application security or performance
- Moderate issues affecting code quality
- Should be planned for future development cycles
- Potential future problems if left unaddressed
- Minor improvements and best practice recommendations
- Good to address during routine maintenance
- Primarily affects code maintainability
CWE Categories
Issues are classified using Common Weakness Enumeration (CWE) standards:- CWE-943 - NoSQL Injection vulnerabilities
- CWE-94 - Code Injection issues
- CWE-79 - Cross-site Scripting (XSS)
- CWE-22 - Path Traversal vulnerabilities
- And many more standardized categories
Best Practices
Regular Scanning
- Before Releases - Scan before deploying to production
- After Major Changes - Analyze code after significant updates
- Weekly Reviews - Regular scans for ongoing projects
- New Dependencies - Scan when adding new packages or libraries
Team Collaboration
- Share Results - Export and share scan reports with your team
- Track Progress - Monitor issue resolution over time
- Set Standards - Establish security and quality thresholds
- Review Together - Use results for code review discussions
Integration with Development Workflow
While AI Scanner is web-based, you can integrate it with your workflow:- Manual Scans - Run scans at key development milestones
- Report Sharing - Download and share results with stakeholders
- Issue Tracking - Use results to create tickets in your project management tools
- Documentation - Include scan results in security documentation
Getting Started
- Sign Up - Create your Gammacode account at https://gammacode.dev
- Connect GitHub - Authorize access to your repositories
- Run First Scan - Start with a security scan on your main repository
- Review Results - Examine findings and understand the recommendations
- Fix Issues - Use one-click fixes or manual remediation
- Track Progress - Regular scans to monitor improvement